Configure KeyCloak SSO in Kestra
Setup KeyCloak SSO to manage authentication for users.
Start a KeyCloak service
If you don’t have a KeyCloak server already running, you can use a managed service like Cloud IAM.
You can follow the steps described here to deploy a managed KeyCloak cluster for free.
Configure KeyCloak client
Once in KeyCloak, you would need to create a client:
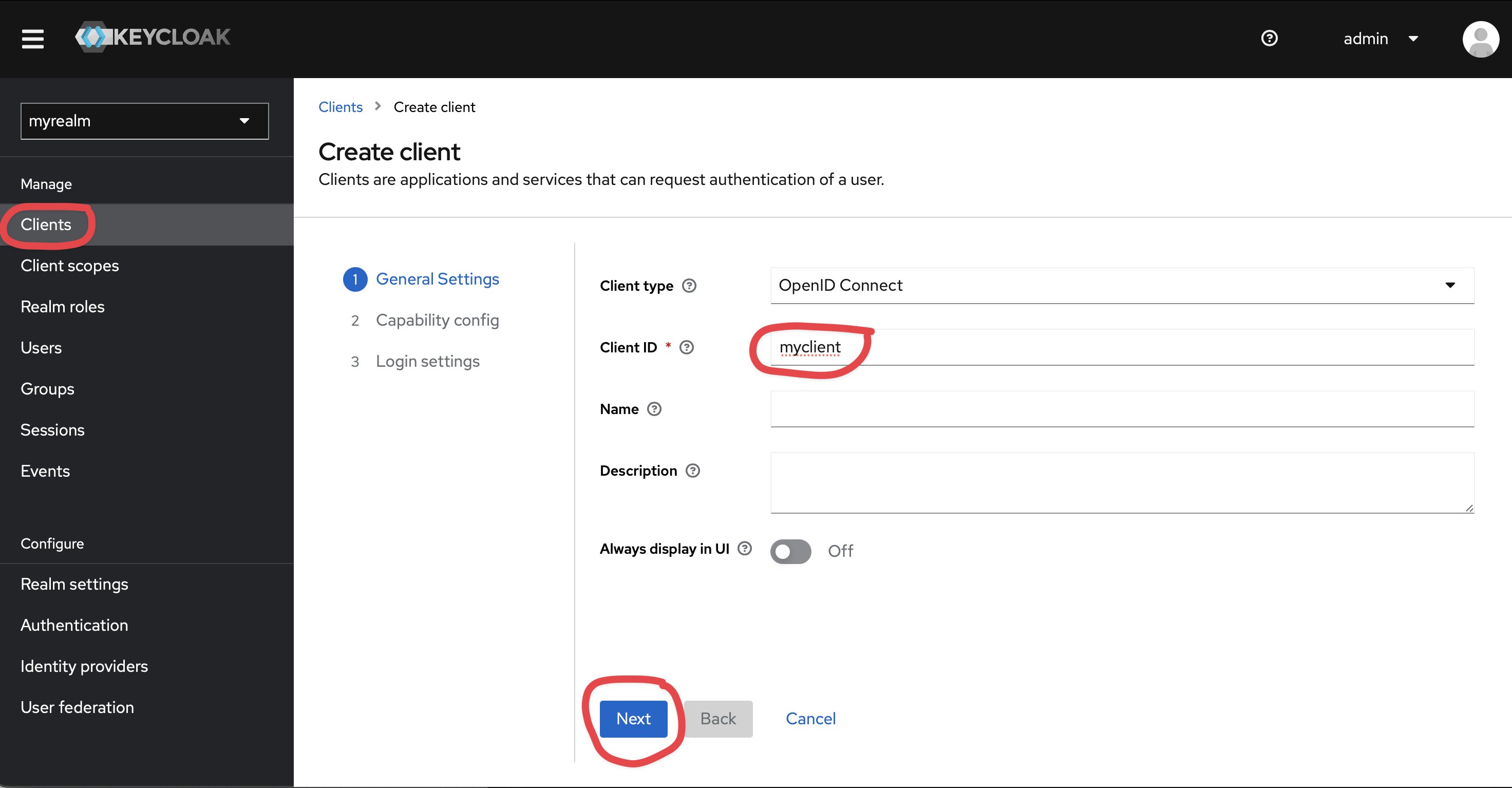
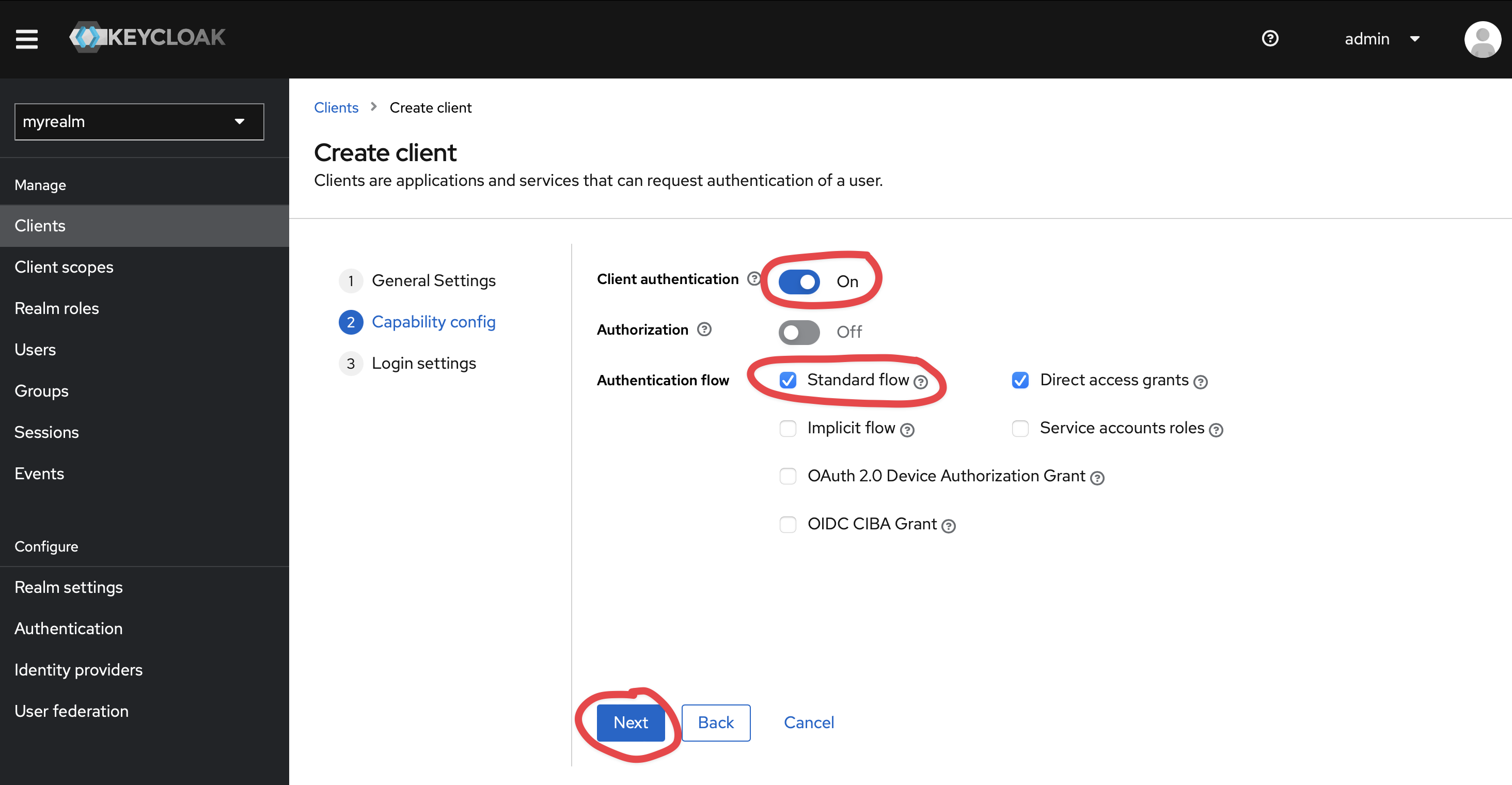
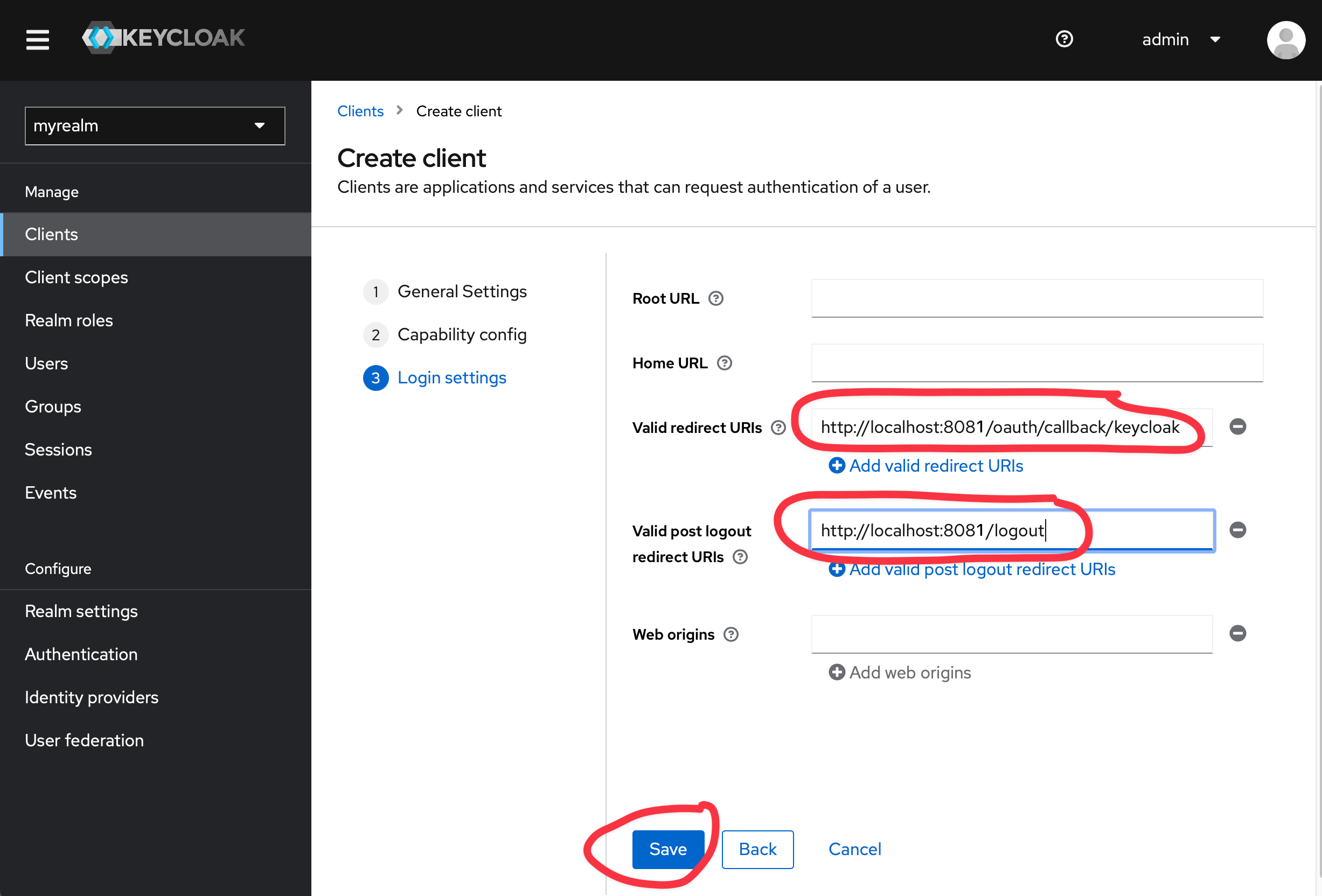
Set https://{{ yourKestraInstanceURL }}/oauth/callback/keycloak as Valid redirect URIs and https://{{ yourKestraInstanceURL }}/logout as Valid post logout redirect URIs.
Kestra Configuration
micronaut: security: oauth2: enabled: true clients: keycloak: client-id: "{{clientId}}" client-secret: "{{clientSecret}}" openid: issuer: "https://{{keyCloakServer}}/auth/realms/{{yourRealm}}" endpoints: logout: get-allowed: trueYou can retrieve clientId and clientSecret via KeyCloak user interface
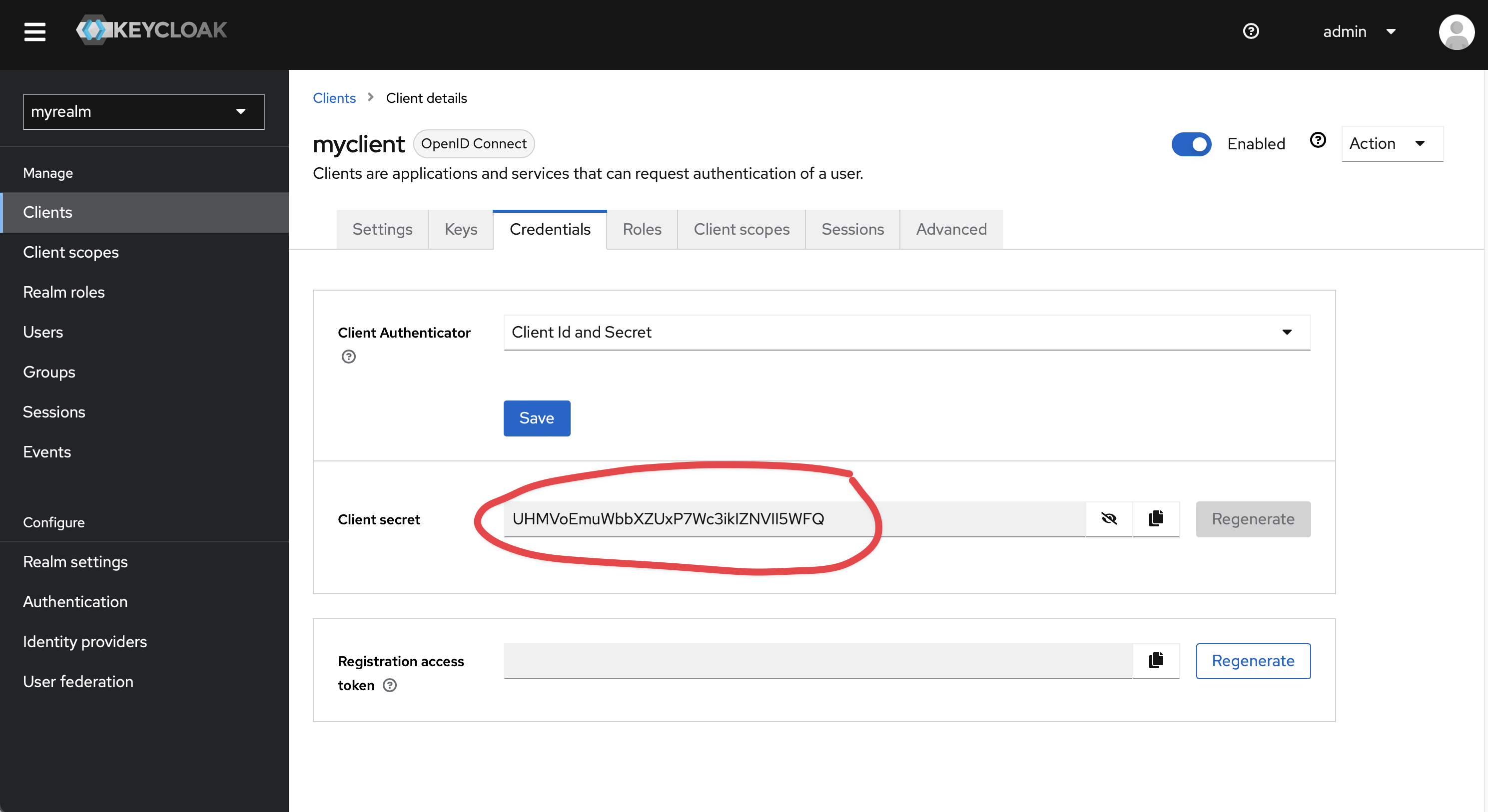
Don’t forget to set a default role in your Kestra configuration to streamline the process of adding new users.
kestra: security: defaultRole: name: Editor description: Default Editor role permissions: FLOW: ["CREATE", "READ", "UPDATE", "DELETE"] EXECUTION: - CREATE - READ - UPDATE - DELETENote: depending of the KeyCloak configuration you might want to tune the issuer url.
For more configuration details, refer to the Keycloak OIDC configuration guide.